mirror of
https://github.com/chillout2k/ExOTA-Milter.git
synced 2026-02-04 00:14:24 +00:00
docs + some OCI enhancements
This commit is contained in:
parent
6c844f22e7
commit
3e9409717f
@ -1,7 +1,7 @@
|
||||
version: '2.4'
|
||||
services:
|
||||
exota-milter:
|
||||
image: chillout2k/exota-milter-amd64
|
||||
image: chillout2k/exota-milter
|
||||
restart: unless-stopped
|
||||
environment:
|
||||
LOG_LEVEL: 'debug'
|
||||
|
||||
@ -45,7 +45,7 @@ spec:
|
||||
path: 'exota-milter-policy.json'
|
||||
containers:
|
||||
- name: exota-milter
|
||||
image: chillout2k/exota-milter-amd64
|
||||
image: chillout2k/exota-milter
|
||||
imagePullPolicy: Always
|
||||
volumeMounts:
|
||||
- mountPath: /data
|
||||
|
||||
@ -6,7 +6,8 @@ LABEL git_repo="https://github.com/chillout2k/exota-milter"
|
||||
ADD ./requirements.txt /requirements.txt
|
||||
|
||||
RUN apk update \
|
||||
&& apk add python3 python3-dev py3-pip gcc libc-dev libmilter-dev \
|
||||
&& apk add --no-cache python3 python3-dev py3-pip \
|
||||
gcc libc-dev libmilter-dev \
|
||||
&& pip3 install -r requirements.txt \
|
||||
&& apk del gcc libc-dev libmilter-dev python3-dev py3-pip \
|
||||
&& apk add libmilter \
|
||||
|
||||
13
README.md
13
README.md
@ -99,8 +99,8 @@ By the way, the global setting `ENV[MILTER_DKIM_ALIGNMENT_REQUIRED]` can be over
|
||||
}
|
||||
```
|
||||
|
||||
## X-MS-Exchange-CrossTenant-Id header (policy binding)
|
||||
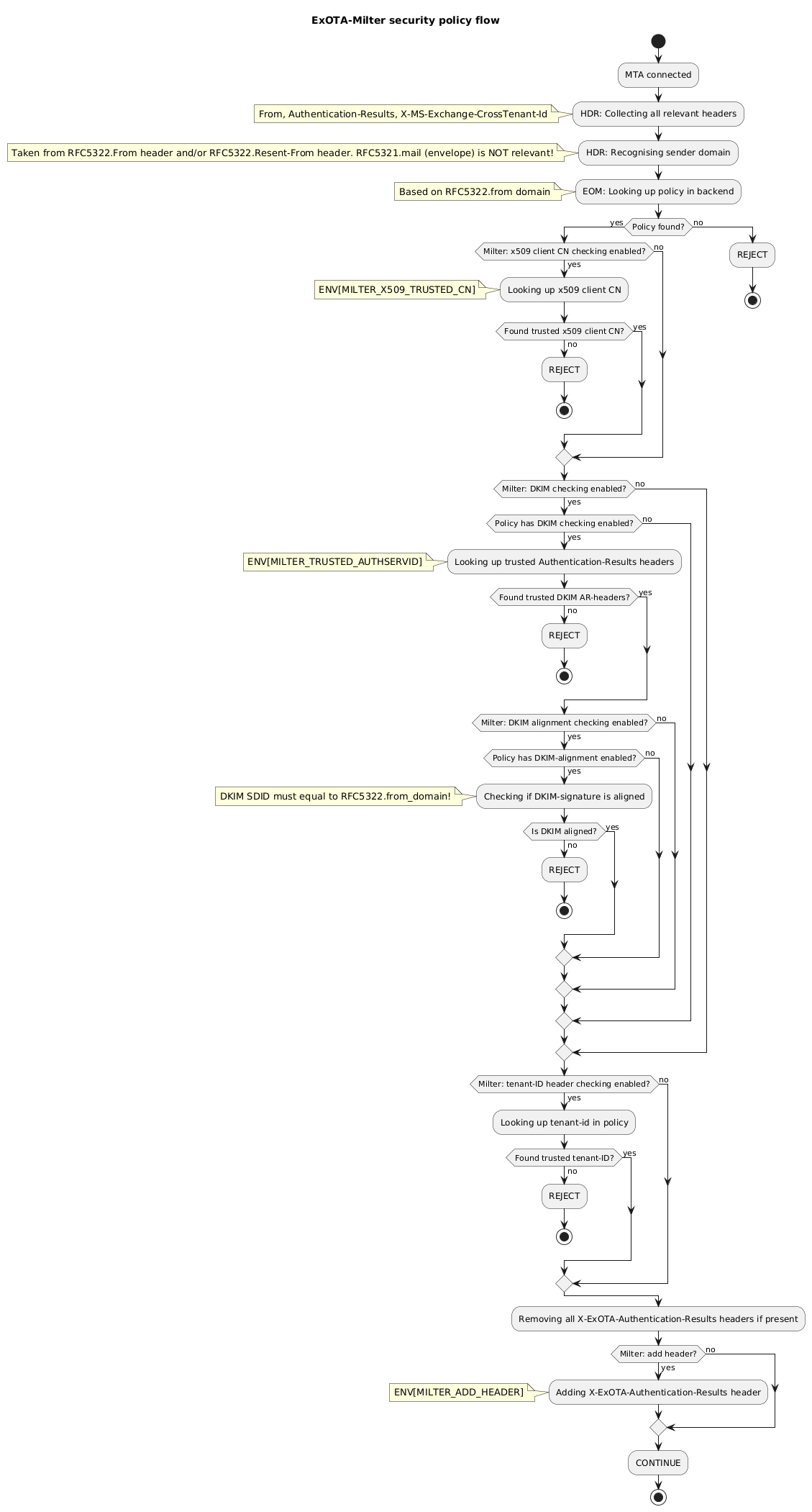
Further each Microsoft Exchange-Online tenant has a unique tenant-ID in form of a UUID ([RFC 4122](https://tools.ietf.org/html/rfc4122)). **ExOTA-Milter** extracts the tenant-ID from the *X-MS-Exchange-CrossTenant-Id* email header and uses it as a *mandatory* authentication factor.
|
||||
## X-MS-Exchange-CrossTenant-Id header (OPTIONAL!)
|
||||
Further each Microsoft Exchange-Online tenant has a unique tenant-ID in form of a UUID ([RFC 4122](https://tools.ietf.org/html/rfc4122)). **ExOTA-Milter** extracts the tenant-ID from the *X-MS-Exchange-CrossTenant-Id* email header and uses it as a *mandatory* authentication factor. Since September 2022 Microsoft did not set this header anymore reliably.
|
||||
```
|
||||
[...]
|
||||
X-MS-Exchange-CrossTenant-Id: <UUID-of-tenant>
|
||||
@ -125,17 +125,18 @@ Finally it´s the combination of all of the above discussed aspects which may re
|
||||
* matching for client certificate´s CN (ExOTA-Milter)
|
||||
* verification of DKIM signatures providing *Authentication-Results* header (another milter, e.g. OpenDKIM)
|
||||
* consideration of DKIM verification results per sender domain (ExOTA-Milter)
|
||||
* matching for tenant-id provided in *X-MS-Exchange-CrossTenant-Id* header (ExOTA-Milter)
|
||||
* *OPTIONAL* matching for tenant-id provided in *X-MS-Exchange-CrossTenant-Id* header (ExOTA-Milter)
|
||||
|
||||
|
||||
|
||||
|
||||
# How about using LDAP as policy backend?
|
||||
For small setups, with not so many domains, the JSON-file policy backend (default) may be sufficient. If you´re an email service provider (ESP) maintaining a lot of customer domains in a LDAP server, you may want to use the LDAP backend instead. Details regarding the LDAP backend can be found [in the LDAP readme](LDAP/README.md).
|
||||
|
||||
# How about a docker/OCI image?
|
||||
## Using prebuilt images from [dockerhub](https://hub.docker.com/)
|
||||
* AMD64: https://hub.docker.com/r/chillout2k/exota-milter-amd64
|
||||
* ARM32v6: https://hub.docker.com/r/chillout2k/exota-milter-arm32v6
|
||||
* **OBSOLETE!** ~~AMD64: https://hub.docker.com/r/chillout2k/exota-milter-amd64~~
|
||||
* **OBSOLETE!** ~~ARM32v6: https://hub.docker.com/r/chillout2k/exota-milter-arm32v6~~
|
||||
* **NEW multi-architecture image:** https://hub.docker.com/repository/docker/chillout2k/exota-milter
|
||||
|
||||
The images are built on a weekly basis. The corresponding *Dockerfile* is located [here](OCI/Dockerfile)
|
||||
|
||||
|
||||
@ -50,11 +50,14 @@ if (Policy found?) then (yes)
|
||||
endif
|
||||
else (no)
|
||||
endif
|
||||
:Looking up tenant-id in policy;
|
||||
if (Found trusted tenant-ID?) then (no)
|
||||
:REJECT;
|
||||
stop
|
||||
else (yes)
|
||||
if (Milter: tenant-ID header checking enabled?) then (yes)
|
||||
:Looking up tenant-id in policy;
|
||||
if (Found trusted tenant-ID?) then (no)
|
||||
:REJECT;
|
||||
stop
|
||||
else (yes)
|
||||
endif
|
||||
else (no)
|
||||
endif
|
||||
else (no)
|
||||
:REJECT;
|
||||
|
||||
Loading…
Reference in New Issue
Block a user